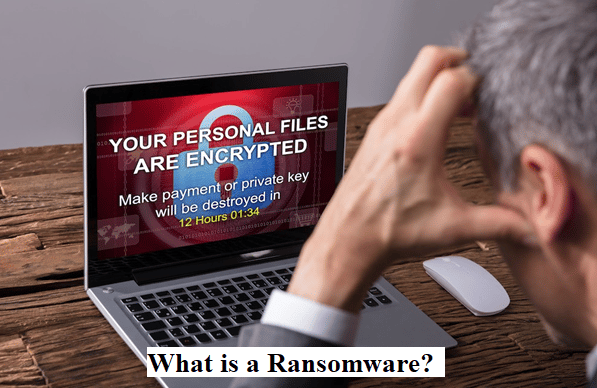
Kidnapping an individual for ransom in the physical world is a very dangerous affair. The turn of events that occur is that; first, the malefactors kidnap the victim, then they keep the victim alive and hidden while they negotiate for paid release. The actual exchange of the victim for the ransom contains a lot of risks and the safety and vitality of the victim cannot be guaranteed.
Content
Computer ransomware, against this threat, is a lot tamer. During a ransomware attack, the malware slips in unobserved and encrypts important files, then demands a ransom in untraceable currency (usually in the form of cryptocurrency). The sole violence which may occur can be the crockery that the distraught victim will throw at the wall out of frustration when they will be locked out of your important files.

If you regularly update your software and do virus scans to keep your computer threat-free, then your antivirus service should indeed wipe out ransomware, a bit like it wipes out other sorts of malware, but on the off chance that it does not, then consequences can often be dire.
Undoubtedly, it is not a great experience to have a virus or Trojan infest your PC, wreak havoc for a couple of days, then get eliminated by an antivirus update, but it surely is survivable. However, when it comes down to the threat of ransomware, that is a different story.
During a ransomware attack, your files would already be encrypted, so eliminating the perpetrator does you no good, and may even interfere with your ability to pay the ransom, in case you opt to do so. The consequences of a ransomware attack can be worse when your whole business falls victim to the hit. Depending on the nature of the business, every hour of lost productivity may cost thousands of dollars, or maybe even more. Fortunately, while ransomware attacks are on the increase, so are techniques for fighting those attacks. Some security products include protection layers specific to ransomware, and you will also be able to add ransomware-specific protection as an added help for your existing security. You can learn more about ransomware. Here we glance at some tools you can use to guard yourself against ransomware.
How to remove Ransomware?
Mr. Trey Turner, a senior adviser at Alagen, says that ransomware can be often removed. While removal of the particular malware is often fairly easy, but the important step of identifying the cause to eliminate persistence of the threat is often, significantly, tougher. He further explains that only getting rid of the ransomware does not necessarily return your access to any encrypted files or systems. Beware that there are not any kind of guarantees. Unfortunately, any decryption attempts — including paying the ransom — might or might not end in you regaining access to encrypted assets. Some ransomware viruses are relatively easy to get rid of, while others are hard.
The simplest ones are ‘scareware’ browser screens that claim your laptop has been locked by the FBI or any police department. You can usually stop them by using the Windows Task Manager to shut the browser, or force quit on MAC, then run a program to get rid of them.
Ransomware predominantly targets windows OS. As backup systems can require many role-based instances for centralized management, data movement, reporting, search, and analytics, securing all those machines are often complex. Consider locking them right down to do only what they are required to do, and nothing more. Newer solutions supported by integrated backup appliances typically remove that complexity and are available- hardened out of the factory.
If the ransomware is detected before a ransom is demanded, you have got the advantage of having the ability to delete the malware. The information that has been encrypted up to the present point remains encrypted, but the ransomware virus can often be stopped. Early detection means the malware can be often prevented from spreading to other devices and files.
In the event of an attack, you can power down the endpoint, reimage it, and reinstall your recent backup. You can have all of your data and you can further prevent the ransomware from spreading to other systems.
There are software tools available (e.g., Norton Power Eraser and Norton Bootable Recovery tool, Malwarebytes) which will remove many threats. A number of the more sophisticated threats could also be much harder to resolve. If your files are encrypted, there could also be a tool available to unencrypt them, counting on the version of the ransomware infection.
Using a malware scanner just like the free Bitdefender virus scanner to look for the ransomware and remove it.
Another thing to note is that it is unlikely you will be the sole person suffering from the ransomware so keep an eye fixed on sites like Macworld to find out more about the nature of the ransomware infection. Ransomware removal tools are only a part of a more comprehensive ransomware protection strategy. This is often because even the foremost effective preventative measures fail occasionally, and cybercriminals are continuously innovating.
Enterprises must assume that occasionally they are going to fall victim to ransomware—if only owing to human error. This suggests that the remainder of the ransomware protection strategy must address a response plan that identifies, quarantines, and removes ransomware infections immediately, and automatically restores data to resume normal operations. Take help from a third-party cybersecurity agency that will take care of attacks. The above methods are all about the automatic method of ransomware removal and data recovery, which helps you to get rid of infections from the machine completely and obtain back your lost or encrypted data with just a few steps. However, it is wiser to hire professional help because even as we are conscious of the answer to a ransomware attack, so are the attackers. While it is relatively simple to get rid of a ransomware infection, getting back your encrypted files without paying the ransom is far tougher.
Mr. Trey Turner, a senior adviser at Alagen, says that ransomware can be often removed. While removal of the particular malware is often fairly easy, but the important step of identifying the cause to eliminate persistence of the threat is often, significantly, tougher. He further explains that only getting rid of the ransomware does not necessarily return your access to any encrypted files or systems. Beware that there are not any kind of guarantees. Unfortunately, any decryption attempts — including paying the ransom — might or might not end in you regaining access to encrypted assets. Some ransomware viruses are relatively easy to get rid of, while others are hard.
The simplest ones are ‘scareware’ browser screens that claim your laptop has been locked by the FBI or any police department. You can usually stop them by using the Windows Task Manager to shut the browser, or force quit on MAC, then run a program to get rid of them.
Ransomware predominantly targets windows OS. As backup systems can require many role-based instances for centralized management, data movement, reporting, search, and analytics, securing all those machines are often complex. Consider locking them right down to do only what they are required to do, and nothing more. Newer solutions supported by integrated backup appliances typically remove that complexity and are available- hardened out of the factory.
If the ransomware is detected before a ransom is demanded, you have got the advantage of having the ability to delete the malware. The information that has been encrypted up to the present point remains encrypted, but the ransomware virus can often be stopped. Early detection means the malware can be often prevented from spreading to other devices and files.
In the event of an attack, you can power down the endpoint, reimage it, and reinstall your recent backup. You can have all of your data and you can further prevent the ransomware from spreading to other systems.
There are software tools available (e.g., Norton Power Eraser and Norton Bootable Recovery tool, Malwarebytes) which will remove many threats. A number of the more sophisticated threats could also be much harder to resolve. If your files are encrypted, there could also be a tool available to unencrypt them, counting on the version of the ransomware infection.
Using a malware scanner just like the free Bitdefender virus scanner to look for the ransomware and remove it.
Another thing to note is that it is unlikely you will be the sole person suffering from the ransomware so keep an eye fixed on sites like Macworld to find out more about the nature of the ransomware infection. Ransomware removal tools are only a part of a more comprehensive ransomware protection strategy. This is often because even the foremost effective preventative measures fail occasionally, and cybercriminals are continuously innovating.
Enterprises must assume that occasionally they are going to fall victim to ransomware—if only owing to human error. This suggests that the remainder of the ransomware protection strategy must address a response plan that identifies, quarantines, and removes ransomware infections immediately, and automatically restores data to resume normal operations. Take help from a third-party cybersecurity agency that will take care of attacks. The above methods are all about the automatic method of ransomware removal and data recovery, which helps you to get rid of infections from the machine completely and obtain back your lost or encrypted data with just a few steps. However, it is wiser to hire professional help because even as we are conscious of the answer to a ransomware attack, so are the attackers. While it is relatively simple to get rid of a ransomware infection, getting back your encrypted files without paying the ransom is far tougher.
How to prevent Ransomware?
Ransomware is growing every year and no organization is immune to its attacks. And it only takes one click by an unsuspecting employee to infect the whole network, spreading rapidly from a local computer through the entire network and network-attached storage (NAS). Although most organizations have end-point cyber security, ransomware and malware can slip through that and even the best anti-virus protection finds it difficult to track internal threats and compromised employees. Traditional antivirus may not detect next-generation ransomware like Locker ransomware which uses asymmetric encryption or more advanced encryption methods and is difficult (if not impossible) to break locally.

The business model for ransomware has also evolved with time, perpetrators apply the same economies of scale to this criminal enterprise as legitimate businesses do to their own products.
In their 2021 spotlight report on ransomware, Risk Sense and Cyber Security Works (CSW) reviewed the rise of ransomware-as-a-service (RAAS). The RAAS model, typified by operations like Ryuk and Revil, uses a franchise system to maximize the return on investment for ransomware developers.
RAAS is a recent development in the industry that has seen a significant rise in the spread of ransomware. RAAS is cloud-based ransomware sold to distributors at a fee; the distributors then oversee the spread of the virus to the innocent public. The RAAS creators often take a cut from the percentage of profits made from victims. Ransomware groups with their technical expertise to develop the malicious software make it available to various other attack groups which then use their own techniques to get it into users’ systems, including phishing campaigns and other methods. This lowers the barrier to entry for criminal groups to infect victims with ransomware, spreading the problem even further.
It is a basic security precaution to ensure that all software is updated with the latest security patches, but it is worth reiterating that breaches continue due to prolonging updating. Just in 2020, the Solarwinds hack could have been prevented for organizations that promptly patch software.
The next three actions should be: prioritize assets and evaluate traffic, micro-segmentation, and adaptive monitoring towards central steps of the zero-trust architecture and which can greatly reduce your risks of an attack.
Make sure your critical computers are backed up. Safest is to have them backed up to an “air-gapped” location, meaning a location that is not connected to your network. Also, make sure that your backups are versioned. It has been found in some cases that the ransomware itself has been backed up. So, you might need to go back to a previous version of a backup.
If you are unfortunate enough to fall victim to a ransomware attack, your immediate instinct might be to pay the fine and get everything back working as soon as you can. Most criminals will indeed remove the ransomware unlock your files once you have opened your wallet, but there is no guarantee. Thus, prevention, before the crime happens, is the surest and safest way.
How to protect computer from ransomware?
Ransomware is fairly new in the market, spread globally between 2013 to 2014. Jonathan Penn, the Director of Strategy at Avasts' observed that over 500,000 computers were affected by Cryptolocker. The variants of the same have caused around $3 million in damages.
With the advent of technology, ransomware developers and attackers are constantly changing and evolving their methods too. Earlier, the ransom demand used to be for a PayPal payment, which now has evolved to payment in the form of Bitcoins because Bitcoins are harder to track. The Bitcoin mode is unsecured and can be easily lost or even stolen, additionally, it is not insured by any governmental bodies providing attackers with the perfect guise of anonymity. Similarly, their past plan of action used to consist of phishing spam emails as the main point of attack, which has evolved to VPN attacks where they attack your system when you disconnect from your VPN and are momentarily unprotected from all kinds of system-comprising threats.
Time and again, when after raising sufficient awareness among companies against ransomware attacks, the attackers have proved that they will evolve their action plans and technologies, as well. It is always wiser to protect and prevent against ransomware than fall victim to it and loss either your encrypted files or your financial assets or, in some cases, both.
As has been mentioned in the preceding paragraphs, ransomware attacks do not usually threaten individuals, but an entire enterprise instead. Companies, big or small, get targeted often. Their attacks are based on poor security systems which are easier to crack.
Let us again quickly go through the list of ways through which we protect and prevent ransomware:
- System updates: software that we use in our computers and systems are constantly updated by their providers. Make sure to always update to the latest version of the software when the update is available. Not updating can pose threats, as was seen with WannaCry 2017 where the companies who did not keep their systems up to date, were vulnerable and fell victim to ransomware attacks.
- Employee awareness: although the phishing spam mails are an outdated mode of ransomware attacks but that does not mean that it is a completely abandoned method for ransomware attacks. Even today, we get countless emails in our spam folder for kinds of services and companies that we never signed up for. One ignorant employee clicking on them open the portal to a ransomware attack company-wide. Raising awareness is the key to keep these human errors at bay. Human errors are inevitable and we learn from our mistakes but, on the other hand, it is wiser to avoid the mistakes that can be avoided easily. Implementing a permission-based security control which will show up every time an employee clicks on any attachment of any mail can always be a good measure against ransomware.
- Backups: Backup is the key against ransomware, it is not a fool proof plan of action but nonetheless it does provide the protection that your company requires and also come in handy for recovering your data in case your company loses it due to some other issue. Backing up in versions is also very important because there have been cases where the system has backed up the ransomware as well, in that case, you can easily access the previous backups to restore data.
- Cloud services: Cloud-based services are designed in such a such that they are harder to exploit. Since cloud services are third-party organizations, they are not connected to your system or software which can provide extra security in case ransomware attacks your whole system and also gets access to the backup files. Hence, using a backup service which is not connected to your main system also becomes evident in protecting against ransomware.
Best Free Anti Ransomware 2021
After gathering and analyzing data from various websites which rate the anti-ransomware, I have compiled this compact list to help you choose better:
Compatible with: Windows 10, macOS, Android, iOS
Free: Yes
Subscriptions: $40 per year for five PCs
It offers real-time monitoring for viruses, malware, spyware, and ransomware protection, is easy to set up, and stays out of your way while you work without popping up with unnecessary notifications. Bitdefender antivirus software has consistently earned top marks for its antivirus protection and usability in various independent testing labs.
- Avast
Compatible with: Windows 8.1, Mac OS X, Windows 8, Windows 7, Windows 10, macOS, Android, iOS
Free: Yes
Subscriptions: $40 ($70 on renewal) for one device yearly, $50 ($90 on renewal) to protect up to 10 devices for a year.
Provides Anti-virus and anti-malware, excellent detection rates, worthwhile upgrades, and doesn’t slow down your system. The best part is that the ransomware protection is included in the free version of the Avast Antivirus platform. For business users, there are paid-for internet security options to cover a range of additional needs and options.
- Sophos
Compatible with: Windows, macOS
Free: Yes
Subscriptions: $42 per year for 10 PCs
The free version of Sophos Home comes with virus protection for three Windows PCs, using the company’s high-scoring anti-malware tool, additionally, it also offers a 30-day trial of the company’s malware removal tool.
- Microsoft Defender
Compatible with: Windows 10
Free: Yes, built into Windows 10
Subscriptions: Windows Defender Advanced Threat Protection is available to corporate users for a fee
Helps you steer clear of unexpected emails and ensures you do not click on suspicious links that may be phishing attempts, you probably can avoid zero-day attacks and ransomware attacks, you can also have a malware protection safety net.
- MalwareBytes
Compatible with: Windows 10 plus macOS, Android
Free: Yes, for the first 14 days (trial days)
Subscriptions: $30 per year for one device, $80 per year for five devices
Malwarebytes is known for providing protection by actively blocking out threats actively also for offering disinfection services for your device.