Web application penetration testing is the process of employing simulation attacks on a system in order to get to sensitive data. The goal is to find out if a system is safe. These attacks can be done on a system from the inside or the outside. They help give information about the target system, find weaknesses in it, and find exploits that could actually break the system. It is an important check on the health of a system that tells testers if they need to fix things or take security measures.
Content
Importance of Penetration Testing
The common phrase we hear when discussing security is vulnerability. When it comes to security testing, we frequently get confused by the term "vulnerability," and I'm sure many of you, my readers, are in the same boat. For the sake of all the readers, let us first get into the terms ‘vulnerability’ and ‘pen-testing.’
So, what exactly is vulnerability? Vulnerability is a term used to describe flaws in a system that can expose it to security threats.
Kinds of Web Penetration Testing
Web applications can be examined for vulnerabilities in two methods. Tests can be devised to simulate either an internal or external attack.
Internal Penetration Testing
As the name suggests, internal pen testing is done within the organisation over LAN, so it includes testing web applications that are hosted on the intranet. This helps find out if the corporate firewall has any holes that could let hackers in.
We always think that attacks can only come from the outside, so internal pen tests are often forgotten or not given much thought. Basically, it includes Malicious Employee Attacks by disgruntled employees or contractors who would have quit but know internal security policies and passwords, Social Engineering Attacks, Simulation of Phishing Attacks, and Attacks using User Privileges or misusing an unlocked terminal.
External Penetration Testing
External attacks from outside the organisation include testing web applications hosted on the internet. Testers act like inexperienced hackers who are unaware of the internal system. To simulate such attacks, testers are given the IP address of the target system and no other information. They must search and scan public web pages for our information about target hosts, then compromise the hosts found.
It consists primarily of testing servers, firewalls, and intrusion detection systems (IDS).
Web Penetration Testing Approach
It can be done in three steps:
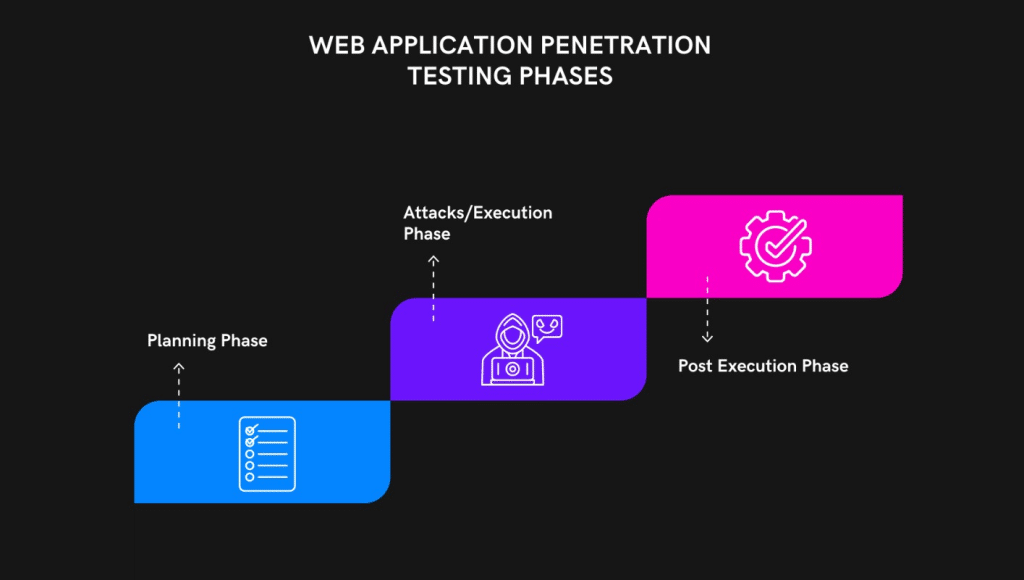
1. Planning Phase (Before Testing)
Before testing begins, it's a good idea to plan out what kind of testing will be done, how it will be done, and whether or not QA needs more access to tools, etc.
- Scope definition: Decide what requires testing before we start.
- Whether or not documentation is available to testers: Make sure the Testers have all the necessary documents, such as those that describe the web architecture, integration points, web services integration, etc. The tester should know the basics of HTTP and HTTPS, as well as how the Web Application Architecture works and how to intercept traffic.
- Determining the Success Criteria: Unlike functional test cases, which can figure out expected results from user requirements and functional requirements, pen-testing works on a different model. Success criteria or criteria for a test case to pass must be set and approved.
- Reviewing the Test Results from Previous Testing: If testing has been done before, it's a good idea to look at the test results to see what weaknesses were there and what steps were taken to fix them. This is always a better way to learn about the testers.
- Understanding the environment: Before the testing starts, testers should learn about the environment. This step should teach them about any firewalls or other security protocols that would need to be turned off for the testing to be done. To test a browser, it should be turned into an attack platform. This is usually done by switching the proxy.
2. As there should not be any limits on ports and services by the internet provider, Web Penetration testing can be conducted from anywhere.
Make sure to test with a variety of user roles, as the system's behaviour could change depending on who is logged in and what permissions they have.
- Testers must report any exploits following the Success Criteria outlined in Phase 1: They must also report vulnerabilities discovered during testing according to the prescribed procedure. Having determined that the system has been breached, the tester now must determine what must be done to fix the situation.
- Making Test Results Public: Penetration testing of web applications is useless to a business if it is not properly reported. In order to guarantee that all relevant parties are informed of the findings of the testing, testers must compile comprehensive reports that describe the vulnerabilities discovered, the testing approach is taken, the severity of the issue, and the exact location of the problem.
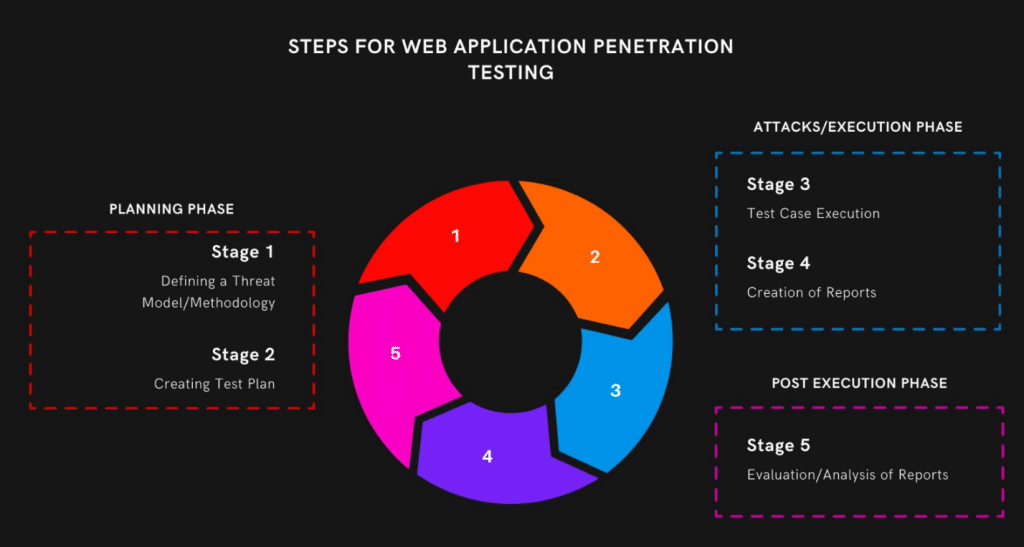
3) Post-Phase (After Testing): Once testing is completed and test reports are distributed to all involved teams, the following list should be worked on by everyone -
- Suggestions for remediation: Pen testing should not stop at identifying vulnerabilities. The concerned team, which should include a QA member, should review the Testers' findings and then discuss the remediation.
- Retest Vulnerabilities: Once the remediation steps have been taken and implemented, testers should retest to ensure that the fixed vulnerabilities did not appear during their retesting.
- Cleanup: As part of the Pentest, testers change the proxy settings, so clean-up should be performed and all changes should be reversed.
Tools used for Web Application Penetration Testing:
The entire penetration testing procedure is heavily dependent on the reconnaissance phase and vulnerabilities found. A comprehensive study makes locating the appropriate exploit and getting system access considerably simpler.
Using resources like web scanners and search engines, you can passively gather information about your target. Use Nmap to scan the target system and identify live ports.
Top Penetration Testing tools:
Some of the tools that can be used for Pentest are listed below:
- Free Pen Test tool
- Veracode
- Vega
- Burp Suite
- Invicti (formerly Netsparker)
- Arachni
- Acunetix
- ZAP
Advantages of Web Application Penetration Testing:
Incorporating web application penetration testing into a security programme has several significant advantages.
- It assists you in meeting compliance requirements. Some industries explicitly require pen testing, and performing web application pen testing helps meet this requirement.
- It aids in the evaluation of your infrastructure. Infrastructure, such as firewalls and DNS servers, is accessible to the public. Any changes to the infrastructure can expose a system to attack. Web application pen testing aids in identifying real-world attacks that may be successful in gaining access to these systems.
- It identifies weaknesses. Web application pen testing identifies application flaws or vulnerable infrastructure routes before an attacker does.
- It aids in the verification of security policies. Web application pen testing looks for flaws in existing security policies.




