Starting as a user with the least amount of access, we try to get into other systems, find sensitive information, gain more access to the network, and move to other parts of the network using a local system and the normal user credentials you give us. As a starting point, the level of access mimics what an attacker might have gotten from a successful phishing email campaign or by pretending to be an employee or contractor. This item is meant to bring attention to the "unknown unknowns" and help your company figure out what can happen and how. In the end, this will help you raise the bar on your internal security.
Content
Pivoting
Pivoting is a method of gaining access to a machine that we do not have direct access to by using an intermediary. The attacker compromises a visible server and then pivots to attack other clients within the network using the compromised server.
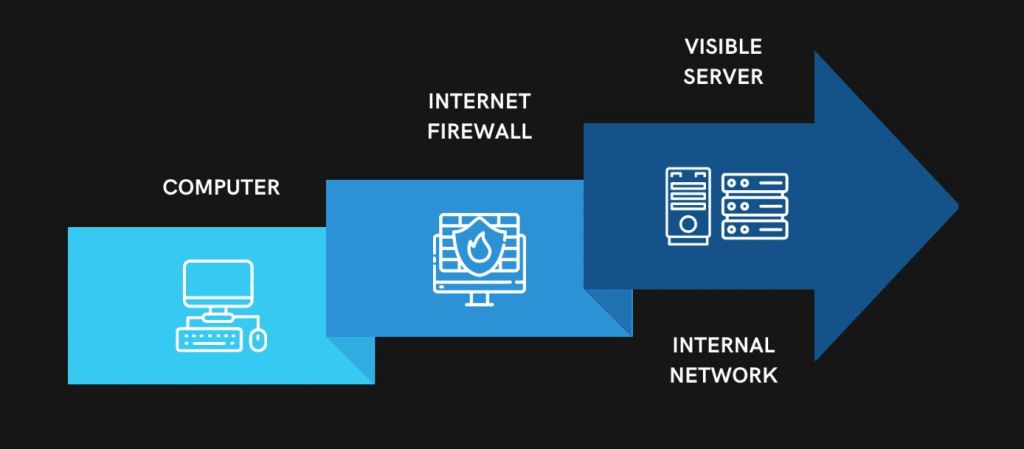
The same thing is shown in the figure above. The attacker takes over a machine or server that is connected to the internet. Then, by using that computer as a middleman, he can get into all the other computers on that network.
Let us examine a case that makes use of pivoting. Imagine we have access to two networks: 192.168.1.0/24, which has been compromised by a hacker.
A private network with the address range 10.10.10.0/24 is not accessible via the internet.
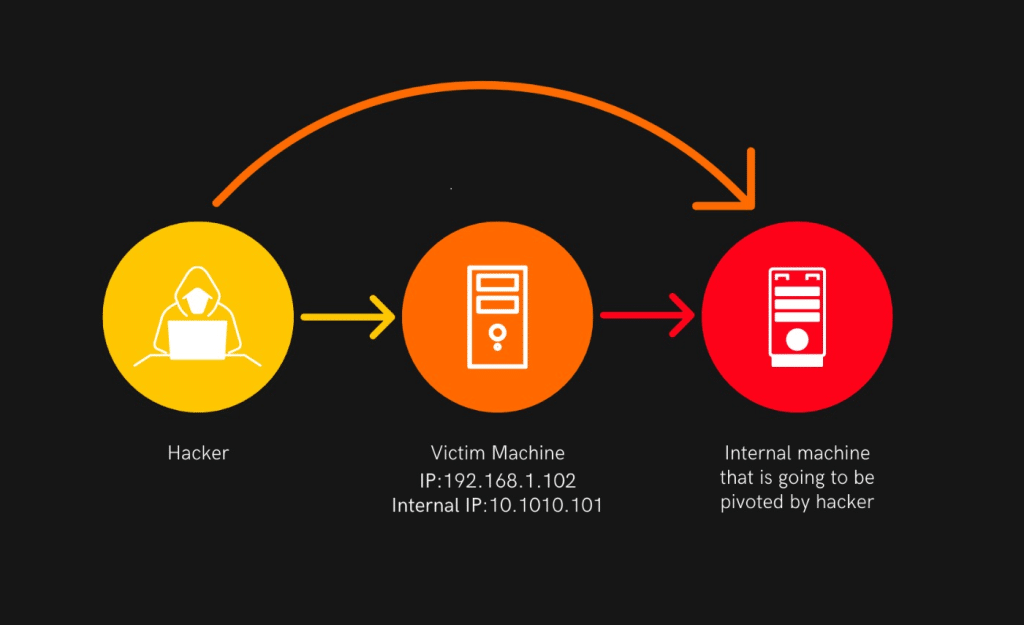
Pivoting Penetration Testing:
During a cyberattack, attackers rarely gain access to the entire network at once. Instead, attackers frequently focus on gaining access to a network via a single flaw. Typically, this is accomplished through techniques such as phishing, malware, or security hole scanning. Once inside the network, the attackers attempt to remain undetected while moving to other systems connected to this point of entry.
When performing a penetration test, pivoting is the process of leveraging a compromised system to move laterally across the network, emulating the actions of a malicious actor. Common names for this corrupted computer system include "instance," "plant," and "foothold."
In search of the most valuable (and susceptible) entry points, penetration testers probe the network for further subnets and machines after gaining a foothold. An administrator machine, for instance, might give the attacker more rights and open up new possibilities. As penetration testers can utilise the compromised machine's credentials and attempt to pass as genuine network traffic, accessing these connected systems is made simpler from the inside.
In cybersecurity, pivoting is closely related to the concept of lateral movement, and the terms are frequently used interchangeably. However, "pivoting" refers to the act of moving from host to host, whereas "lateral movement" includes privilege escalation (gaining access to other users and accounts) on the same machine.
Types of Pivoting Penetration Testing:
Several methods exist for penetration testers to execute pivoting. Listed below are some of the most prevalent methods of pivoting in penetration testing:
Port forwarding:
The attacker makes a tunnel between two machines by using open TCP/IP ports to send packages and traffic from one to the other. There are different ways to forward ports:
- Local port forwarding: The compromised machine "listens" for data and instructions from the attacker's machine, giving the attacker access to internal services.
- Remote port forwarding: When an attacker maps ports on their machine to local ports on the compromised machine. This lets them use an SSH connection to reach internal services.
- Dynamic port forwarding: The attacker sets up a SOCKS proxy server for tunnelling traffic. The compromised machine acts as a middleman between the attacker's machine and internal services.
VPN pivoting:
The attacker starts a virtual private network (VPN) client on the computer he or she has control over and connects to a VPN server in another location. The attacker then sends data to the client from the server. By sending data from the client to the server, the attacker can also get information (like network traffic) from the machine that was compromised.
Proxy pivoting/SSH pivoting:
The attacker sets up an SSH server that acts as a local proxy server. The proxy then sends any connections to the specified port to their final destination.
Routing tables:
The attacker adds a new route by changing the machine's routing table. With this route, all traffic going to the destination will have to tunnel through the defined gateway, which lets the attacker get this data.In penetration testing, the goal is to undertake reconnaissance and get access to vital files and information while staying unnoticed for as long as feasible.




